Bash snippets: Difference between revisions
Jump to navigation
Jump to search
Content added Content deleted
(search paths) |
(add image) |
||
| (2 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
__TOC__ |
__TOC__ |
||
=== Prompts === |
|||
<source lang="Bash"> |
|||
export PS1='\[\033[0;32m\][\[\033[0;31m\]\u@\h \[\033[0;34m\]\w \[\033[0;33m\]$?\[\033[0;32m\]]\n\[\033[0m\]\$\[\033[0m\] ' |
|||
</source> |
|||
[[File:prompt.png|thumb|Example output.]] |
|||
Output (modulo colours): |
|||
<pre> |
|||
[vegard@t460 ~ 0] |
|||
$ |
|||
</pre> |
|||
See also: http://man7.org/linux/man-pages/man1/bash.1.html#PROMPTING |
|||
=== Adding to the search path === |
=== Adding to the search path === |
||
| Line 9: | Line 25: | ||
This is more secure than plain appending, which can create empty components (e.g. a trailing ":") which are interpreted as "current directory" and lead to [https://threatpost.com/some-linux-distros-vulnerable-version-dll-hijacking-bug-082610/74387/ DLL search order hijacking]. |
This is more secure than plain appending, which can create empty components (e.g. a trailing ":") which are interpreted as "current directory" and lead to [https://threatpost.com/some-linux-distros-vulnerable-version-dll-hijacking-bug-082610/74387/ DLL search order hijacking]. |
||
[[Category:Programming]] |
|||
Latest revision as of 08:57, 9 April 2020
Prompts
export PS1='\[\033[0;32m\][\[\033[0;31m\]\u@\h \[\033[0;34m\]\w \[\033[0;33m\]$?\[\033[0;32m\]]\n\[\033[0m\]\$\[\033[0m\] '
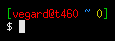
Output (modulo colours):
[vegard@t460 ~ 0] $
See also: http://man7.org/linux/man-pages/man1/bash.1.html#PROMPTING
Adding to the search path
# https://stackoverflow.com/a/9631350/1697183
export LD_LIBRARY_PATH="/foo/bar${LD_LIBRARY_PATH:+:$LD_LIBRARY_PATH}"
This is more secure than plain appending, which can create empty components (e.g. a trailing ":") which are interpreted as "current directory" and lead to DLL search order hijacking.